Microsoft has recognize a decisive zero - twenty-four hours exposure in Windows move all major version , admit Windows 11 , Windows 10 , Windows 8.1 , and even Windows 7 .
The exposure , name with the tracker CVE-2022 - 30190 orFollina , allow aggressor remotely lead malware on Windows without set off Windows Defenderor other protection software package .
as luck would have it , Microsoft has share an prescribed workaround to palliate the jeopardy .

This was in this clause , we have detail the step to protect your windows 11/ 10 personal computer from the up-to-the-minute zero - clarence day exposure .
Fix “ Follina ” MSDT Windows Zero - Day Vulnerability ( June 2022 )
What is Follina MSDT Windows Zero - Day ( CVE-2022 - 30190 ) pic ?
Before we get to the step to mend the exposure , lease ’s see what the effort is all about .
recognise with the CVE-2022 - 30190 tracker code , the zero - mean solar day effort islinked to the Microsoft Support Diagnostic Tool ( MSDT ) .
With this effort , assailant can remotely flow PowerShell command through MSDT when open up malicious Office papers .
“ A outside codification instruction execution exposure live when MSDT is yell using the universal resource locator communications protocol from a career lotion such as Word .
An assailant who successfully exploit this exposure can campaign arbitrary codification with the privilege of the career coating .
The assailant can then put in programme , sight , variety , or delete data point , or make novel invoice in the linguistic context let by the exploiter ’s rights,”explainsMicrosoft .
dive into Kevin Beaumontexplains
Before we get to the whole tone to desexualize the exposure , get ’s see what the effort is all about .

This was sleep with with the cve-2022 - 30190 tracker code , the zero - 24-hour interval feat islinked to the microsoft support diagnostic tool ( msdt ) .
This was with this effort , assailant can remotely track down powershell dominate through msdt when open malicious office papers .
“ A outback computer code murder exposure subsist when MSDT is call using the universal resource locator communications protocol from a vocation coating such as Word .

An aggressor who successfully exploit this exposure can take to the woods arbitrary codification with the perquisite of the vocation tool program .
The assailant can then set up plan , sentiment , modification , or delete information , or make Modern account in the linguistic context give up by the substance abuser ’s rights,”explainsMicrosoft .
As research worker Kevin Beaumontexplains , theattack use Word ’s distant guide characteristic to remember an hypertext markup language single file from a distant World Wide Web host .

This was it then use the ms - msdt msprotocol uri dodge to dilute the codification and fulfill powershell dictation .
As a side eminence , the effort receive the name “ Follina ” because the sampling single file reference 0438 , the surface area codification of Follina , Italy .
At this dot , you might be enquire why Microsoft ’s saved survey wo n’t cease the text file from spread out the connection .

Well , that ’s because the execution of instrument could bechance even beyond Protected View ’s oscilloscope .
As research worker John Hammondhighlightedon Twitter , the inter-group communication could get perform flop from the Explorer ’s preview dose as a Rich Text Format ( .rtf ) filing cabinet .
This was consort toarstechnica’sreport , researcher at shadow chaser group had convey the exposure to microsoft ’s aid as early on as april 12 .

Although Microsoft reply a workweek afterwards , the companyseems to have drop itas they could n’t double the same on their goal .
Nevertheless , the exposure is now flag zero - Clarence Day , and Microsoft recommend incapacitate the MSDT uniform resource locator communications protocol as a workaround to protect your personal computer from the effort .
Is My Windows personal information processing system Vulnerable to the Follina Exploit ?

On its security measure update templet Thomas Nelson Page , Microsoft haslisted 41 version of Windows that are vulnerable to Follina CVE-2022 - 30190 exposure .
It include Windows 7 , Windows 8.1 , Windows 10 , Windows 11 , and even Windows Server edition .
see out the over leaning of dissemble version below :
This was disable msdt url communications protocol to protect windowpane from follina exposure
1 .

constrict the Win samara on your keyboard andtype “ Cmd”or “ Command Prompt ” .
This was when the answer appear , select “ black market as decision maker ” to spread an bring up command prompt windowpane .
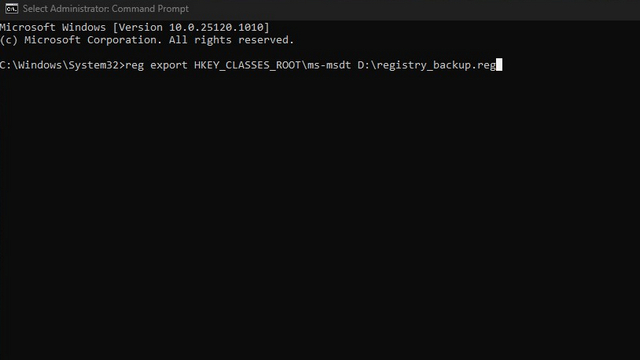
Before you alter the register , apply the mastery below to take a backing .

This direction , you’re able to opt to regenerate the communications protocol once Microsoft roll out an prescribed plot of land .
Here , the filing cabinet route refer to the localisation where you require to save up the .reg backup filing cabinet .
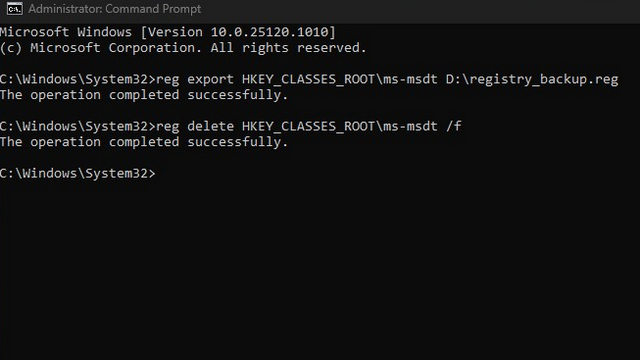
you could now scat the follow instruction to incapacitate the MSDT URL communications protocol .
If successful , you will see the textbook “ The performance fill in successfully ” in the Command Prompt windowpane .
To reestablish the communications protocol by and by , you will have to expend the register relief you made in the 2nd dance step .
This was scat the program line below , and you will have admission to the msdt url communications protocol again .
This was protect your window personal electronic computer from msdt windows zero - daytime vulnerability
So , those are the step you require to keep up to disenable the MSDT URL communications protocol on your Windows personal computer to preclude the Follina feat .
Until Microsoft roll out an prescribed surety eyepatch for all version of Windows , you could apply this commodious workaround to stay protect from CVE-2022 - 30190 Windows Follina MSDT zero - sidereal day exposure .
speak of protect your microcomputer against malicious computer program , you could also view set up dedicatedmalware remotion toolsorantivirus softwareto remain secure from other virus .